Amazon Web Services (AWS) Identity and Access Management (IAM) is a web service that helps organizations securely control access to AWS resources. IAM enables organizations to create and manage users and groups, and to use permissions to allow and deny their access to AWS resources. IAM is a critical service for organizations using AWS, because it helps to ensure that only authorized users have access to the organization's resources. With IAM, organizations can create and manage users and groups, and define their permissions to access AWS resources. This helps to improve security and compliance, and to reduce the risk of unauthorized access to sensitive data and resources.

To create an IAM service in AWS, you will first need to sign in to the AWS Management Console. From there, you can access the IAM service by clicking on the "Services" menu and selecting "IAM" from the list of services.
Once you are in the IAM service, you can create a new IAM user by clicking on the "Users" menu and then clicking on the "Add User" button. You will then be prompted to enter a name for the user, as well as to select the type of access that you want to grant the user.
After you have created the user, you can manage their access by attaching IAM policies to the user. IAM policies specify which actions the user is allowed to perform, as well as which AWS resources they are allowed to access.
IAM is a powerful service that allows you to securely manage access to your AWS resources. By creating IAM users and attaching appropriate policies to them, you can ensure that only authorized users have access to your AWS resources.
To create an IAM user using the AWS CLI, you will need to have the AWS CLI installed and configured on your computer. Once you have the AWS CLI installed, you can create an IAM user by using the aws iam create-user command.
Here is an example of how to create an IAM user using the AWS CLI:
aws iam create-user --user-name my-new-user
This command will create a new IAM user with the user name "my-new-user".
Once you have created the IAM user, you can manage their access by attaching IAM policies to the user. To do this, you can use the aws iam attach-user-policy command.
Here is an example of how to attach an IAM policy to an IAM user using the AWS CLI:
aws iam attach-user-policy --user-name my-new-user --policy-arn arn:aws:iam::aws:policy/AmazonS3ReadOnlyAccess
This command will attach the AmazonS3ReadOnlyAccess policy to the my-new-user user, which will allow them to access Amazon S3 with read-only permissions.
By using the AWS CLI, you can easily create and manage IAM users and their access to AWS resources. This can be a convenient way to manage your AWS environment, especially if you have a large number of IAM users to manage.
IAM Best Practices
Here are some best practices for using AWS Identity and Access Management (IAM):
Use IAM to grant least privilege: Only grant the minimum permissions necessary to perform a task. This helps reduce the risk of unintended actions or data leaks.
Use IAM groups to manage permissions: Instead of granting permissions directly to users, create IAM groups and assign permissions to the group. This makes it easier to manage permissions for multiple users at once.
Use IAM policies to grant permissions to resources: Use resource-based policies to grant permissions to specific resources, rather than granting permissions to users or groups directly. This allows you to fine-tune permissions for each resource.
Use multi-factor authentication (MFA) for sensitive accounts: Enable MFA for any IAM user with administrative privileges to add an extra layer of security.
Rotate access keys regularly: Access keys are used to programmatically access AWS services. It's a good idea to rotate these keys regularly to reduce the risk of them being compromised.
Monitor IAM activity: Use CloudTrail to monitor and audit IAM activity, including changes to permissions and the use of access keys. This can help you detect and prevent unauthorized access.
For more information about IAM best practices, see the AWS IAM documentation.
Different Types of Policies
In AWS Identity and Access Management (IAM), there are three types of policies:
- Identity-based policies: These policies are attached directly to IAM users, groups, or roles. They grant permissions to the associated identity.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:GetObject",
"Resource": ["arn:aws:s3:::mybucket/*"]
},
{
"Effect": "Deny",
"Action": "ec2:RunInstances",
"Resource": "*"
}]
}
Resource-based policies: These policies are attached to specific AWS resources, such as an S3 bucket or an EC2 instance. They grant permissions to access the resource to specified identities.
{ "Version":"2012-10-17", "Statement":[ { "Effect":"Allow", "Principal": "*", "Action":["s3:GetObject"], "Resource":["arn:aws:s3:::mybucket/*"] } ] }Permission boundaries:

These policies define the maximum permissions that can be granted to an IAM user or role. They can be used to set limits on the permissions that can be granted to identities in an organization.
Identity-based policies are the most commonly used type of policy, as they allow you to grant permissions directly to users, groups, or roles. Resource-based policies are useful when you want to grant permissions to specific resources, rather than to identities. Permission boundaries can be used to set limits on the permissions that can be granted to an IAM user or role, helping to enforce least privilege and prevent over-provisioning of permissions.
Policy Evaluation
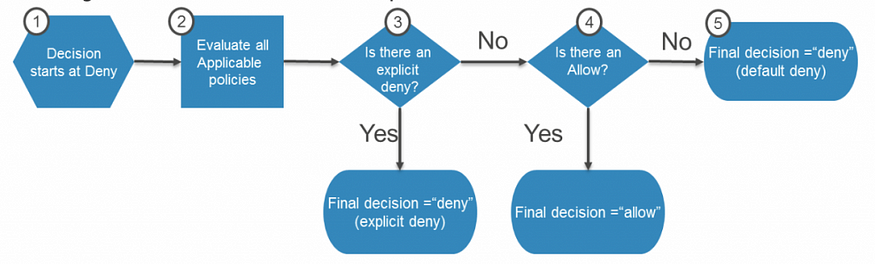
In AWS Identity and Access Management (IAM), policy evaluation is the process of determining whether a request to perform an action on a resource is allowed or denied.
During policy evaluation, IAM compares the action and resource specified in the request to the permissions granted in the IAM policies that are associated with the identity making the request. If the action and resource are allowed by one of the policies, the request is allowed. If the action and resource are not allowed by any of the policies, the request is denied.
IAM evaluates policies in the following order:
IAM identity-based policies (policies that are directly attached to the identity making the request)
Resource-based policies (policies that are attached to the resource being accessed)
Permission boundaries (policies that define the maximum permissions that can be granted to an IAM user or role)
If a request is allowed by multiple policies, IAM grants the permissions that are most permissive. For example, if a policy allows read access to an S3 bucket and another policy allows read and write access to the same bucket, the user will have read and write access to the bucket.
Identity Federation
Identity federation is a way to allow users to use existing login credentials (such as their corporate username and password) to access AWS resources. With identity federation, you can grant users access to AWS resources without creating an IAM user for each user.
There are several ways to set up identity federation in AWS:
SAML 2.0: You can use Security Assertion Markup Language (SAML) 2.0 to enable users to use single sign-on (SSO) to access AWS resources. This allows users to log in to AWS using their corporate credentials and access authorized resources without having to create an IAM user for each user.
Web identity federation: You can use web identity federation to allow users to authenticate with public identity providers such as Amazon, Facebook, or Google. This allows users to access AWS resources using their existing login credentials from these providers.
Cross-account IAM roles: You can use cross-account IAM roles to grant permissions to users in another AWS account. This allows users in one account to access resources in another account without the need to create IAM users in the target account.
STS API Methods
AWS Security Token Service (STS) is a web service that enables you to request temporary, limited-privilege credentials to access AWS resources. STS is often used in conjunction with identity federation to grant temporary access to AWS resources.
Here are some of the API methods available in STS:
AssumeRole: This method enables you to assume an IAM role and obtain temporary security credentials. You can specify the duration of the session and the permissions to be granted by the role.
GetCallerIdentity: This method returns the AWS Identity and Access Management (IAM) user or role that made the request. You can use this method to confirm the identity of the caller.
GetFederationToken: This method enables you to request a set of temporary security credentials that you can use to access AWS resources. You can specify the duration of the session and the permissions to be granted by the token.
GetSessionToken: This method returns a set of temporary security credentials that you can use to access AWS resources. You can specify the duration of the session and the permissions to be granted by the token.
