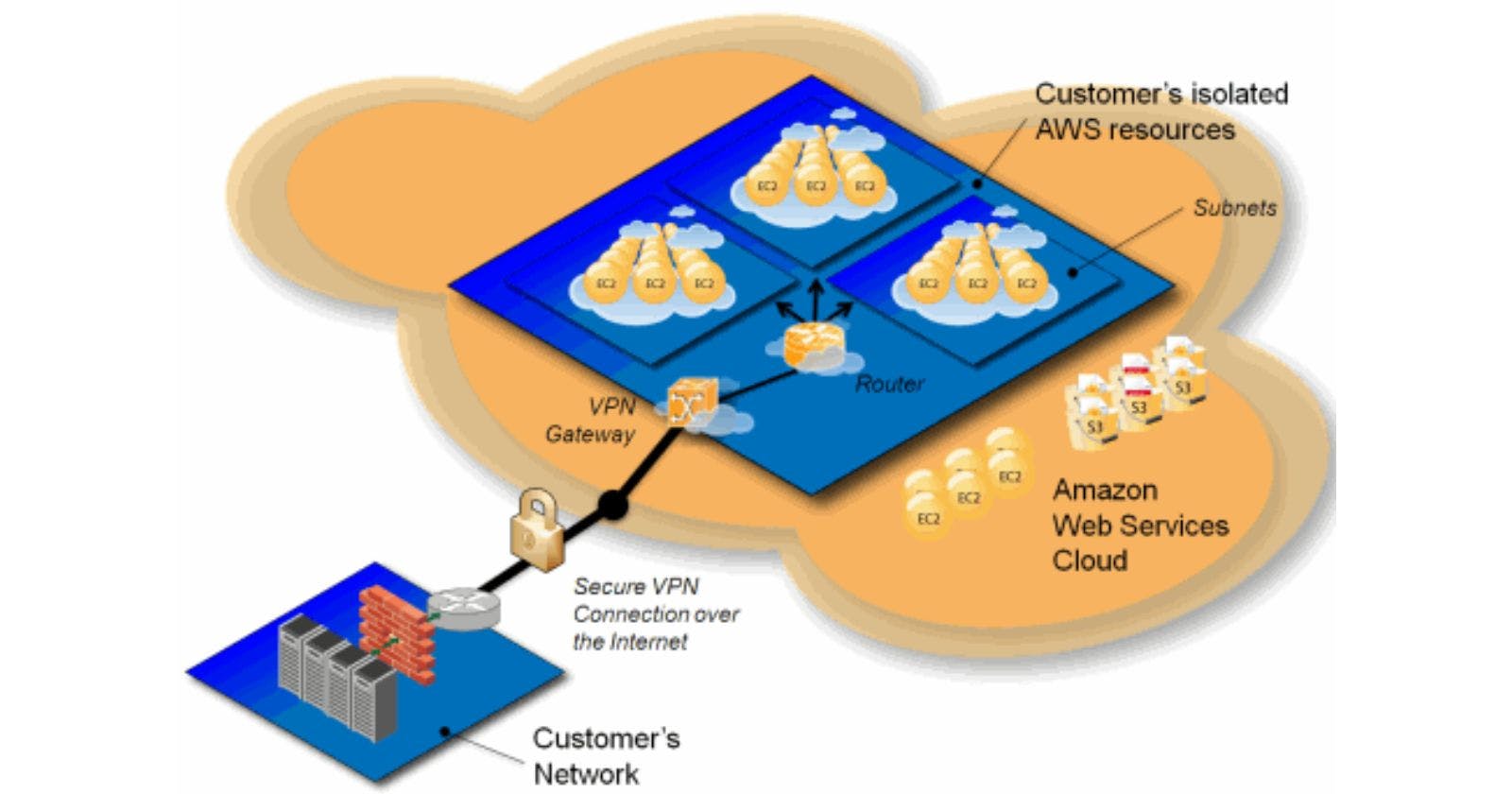
Amazon Virtual Private Cloud (Amazon VPC) is a service that lets you launch Amazon Web Services (AWS) resources in a virtual network that you define. This virtual network closely resembles a traditional network that you might operate in your own data centre, with the benefits of using the scalable infrastructure of AWS.
With Amazon VPC, you can define a virtual network topology that closely resembles your own network, with a range of IP addresses, subnets, and network gateways. You can also specify security and access control lists, and network access control lists (ACLs). You can use Amazon VPC to launch Amazon Elastic Compute Cloud (Amazon EC2) instances, Amazon Relational Database Service (Amazon RDS) instances, and other AWS resources in this virtual network.
Why use a VPC?
There are several reasons why you might want to use a virtual private cloud (VPC) in Amazon Web Services (AWS):
Security:A VPC allows you to create a logically isolated section of the AWS Cloud where you can launch your AWS resources. You can control the network access to your resources using security groups and network access control lists (ACLs).Custom IP address range:With a VPC, you can specify the IP address range for your virtual network, as well as the subnets within that range. This allows you to create a virtual network that closely resembles your own on-premises network.Network isolation:A VPC allows you to create a logically isolated section of the AWS Cloud where you can launch your AWS resources. This means that your resources are isolated from other customers' resources, which can be beneficial in a multi-tenant environment.Connectivity options:A VPC allows you to connect your virtual network to the internet, your on-premises data center, or other virtual networks within AWS. You can also use a VPC to host multi-tier applications, test new software, or to extend your on-premises data center into the cloud.Flexibility:A VPC allows you to customize the network configuration of your virtual network to meet your specific needs. You can create multiple subnets in a VPC and launch resources in different subnets, depending on your networking requirements.
CIDR
Classless Inter-Domain Routing (CIDR) is a method of allocating IP addresses and routing Internet Protocol packets. It replaces the older system based on classes A, B, and C.

In CIDR notation, an IP address is written as a base IP address, followed by a slash (/), followed by a number called the network prefix. The network prefix specifies the number of leading bits of the IP address that are used to identify the network. For example, the network prefix /24 represents the first 24 bits of the IP address, which specifies the network. The remaining bits of the IP address represent the host within the network.
CIDR allows for more flexible and efficient allocation of IP addresses, as it allows a single IP address to represent a network of any size. It also allows for the aggregation of multiple IP address ranges, which helps reduce the size of routing tables and improve the efficiency of routing.
CIDR is widely used in the Internet and in other networks to specify IP address ranges and to route traffic between networks. It is also used in Amazon Virtual Private Cloud (Amazon VPC) to specify the IP address range for a VPC and the subnets within that range.
Internet Gateway
An Internet gateway is a VPC component that allows communication between instances in your VPC and the Internet. It therefore imposes a public IP address on the instances in your VPC, allowing them to communicate with the Internet via the Internet gateway.
The Internet gateway is a virtual router that connects your VPC to the Internet. It routes traffic between your VPC and the Internet, allowing instances in your VPC to communicate with the Internet, and allowing Internet traffic to reach your VPC.
You can create an Internet gateway and attach it to your VPC. Once attached, you can then configure your VPC subnets to route traffic to the Internet gateway. This allows instances in those subnets to communicate with the Internet. You can also create route tables and specify the Internet gateway as the target for Internet-bound traffic.
An Internet gateway is a key component of a VPC, as it allows instances in your VPC to communicate with the Internet. It is therefore necessary to create an Internet gateway and attach it to your VPC if you want your instances to be able to communicate with the Internet.
Subnet
In Amazon Virtual Private Cloud (Amazon VPC), a subnet is a range of IP addresses in your VPC. You can select its IP address range from your VPC's IP address range, and you can associate security groups and network ACLs with your subnet.
You can use subnets to divide your VPC into multiple networks, and to launch Amazon Elastic Compute Cloud (Amazon EC2) instances in a specific subnet. This can be useful for a variety of reasons, such as:
Isolating the resources of different applications or workloads within your VPC.
Improving the security of your VPC by placing resources in different subnets and applying security groups and network ACLs to each subnet.
Segmenting your VPC into smaller networks to improve network performance.
Enabling you to use different network configurations for different applications or workloads.
Enabling you to use different Amazon Elastic Block Store (Amazon EBS) volumes for different applications or workloads.
When you create a VPC, you must specify a IP address range for the VPC. You can then create subnets within this range, and specify the IP address range for each subnet. Each subnet must be associated with a specific Availability Zone (AZ) within the VPC.
You can also specify the default gateway for each subnet, which can be an Internet gateway, a virtual private gateway, or a NAT gateway. This allows instances in the subnet to communicate with other networks, such as the Internet or on-premises networks.
Route table
In Amazon Virtual Private Cloud (Amazon VPC), a route table contains a set of rules, called routes, that are used to determine where network traffic is directed. Each subnet in a VPC must be associated with a route table, which controls the traffic to and from the subnet.
A route table consists of a set of rules, called routes, that are used to determine where network traffic is directed. Each route in a route table specifies a destination for the traffic and a target for the traffic to reach that destination. The target can be a specific Amazon Elastic Compute Cloud (Amazon EC2) instance, a NAT gateway, or a virtual private gateway, among others.
You can create multiple route tables in a VPC and associate them with different subnets. This allows you to specify different routing rules for different subnets, depending on your networking requirements. For example, you might want to route traffic between subnets within your VPC using one route table, and route Internet-bound traffic using another route table.
You can also create custom routes in a route table and specify the target for the traffic. This allows you to create more complex routing configurations, such as routing traffic to a specific Amazon EC2 instance or to a specific VPC peering connection.
Overall, a route table is an important component of a VPC, as it controls the traffic to and from the subnets in the VPC. It allows you to specify the routing rules for your VPC and customize the routing of traffic to meet your specific needs.
Elastic Network Interface
An Elastic Network Interface (ENI) is a virtual networking component in Amazon Virtual Private Cloud (Amazon VPC) that represents a network interface for an Amazon Elastic Compute Cloud (Amazon EC2) instance. An ENI can include one or more private IP addresses, one Elastic IP address (EIP), and one public IP address.
An ENI is attached to an Amazon EC2 instance and provides the instance with network connectivity. You can create multiple ENIs for an Amazon EC2 instance, allowing the instance to have multiple network interfaces and IP addresses.

An ENI can be associated with a security group, which controls inbound and outbound traffic to and from the ENI. You can also attach an ENI to a subnet in a VPC, which determines the availability zone (AZ) and the IP address range for the ENI.
An ENI is a key component of Amazon VPC, as it allows you to customize the network configuration of your Amazon EC2 instances and to specify the IP address range, security group, and subnet for each ENI. You can use ENIs to create multi-tier applications, to test new software, or to extend your on-premises data center into the cloud.
Elastic IP Address
An Elastic IP is a static public IP address that we can attach to our AWS Account. These IPs are fixed, unlike public IPs which change on instance termination. We can allocate an IP from AWS managed IP or bring our own IP to AWS.
Security Group
In Amazon Virtual Private Cloud (Amazon VPC), a security group acts as a virtual firewall for your Amazon Elastic Compute Cloud (Amazon EC2) instances. It controls inbound and outbound traffic to and from your instances, based on the rules that you specify.

A security group is a set of firewall rules that determine the traffic that is allowed to and from your Amazon EC2 instances. You can create security groups and specify the inbound and outbound rules that apply to them. For example, you might create a security group that allows inbound traffic on port 80 (HTTP) and outbound traffic on port 22 (SSH), but blocks all other traffic.
Network Access Control List
A network access control list (ACL) is a virtual firewall for Amazon Virtual Private Cloud (Amazon VPC) that controls inbound and outbound traffic at the subnet level. It provides an additional layer of security for your VPC, in addition to security groups, which control traffic at the instance level.
A network ACL is a set of rules that specify the traffic that is allowed to and from a subnet in a VPC. You can create multiple network ACLs and associate them with different subnets in your VPC, depending on your networking requirements.
NAT Gateway
A NAT (Network Address Translation) gateway is a Amazon Virtual Private Cloud (Amazon VPC) component that allows instances in a private subnet to connect to the Internet or other Amazon VPCs, while preventing the Internet from initiating connections with those instances. NAT gateways enable instances in a private subnet to initiate outbound connections to the Internet or other VPCs, but prevent the Internet from initiating connections with those instances.
A NAT gateway is a virtual router that provides the ability for instances in a private subnet to connect to the Internet or other VPCs, while providing an additional layer of security for those instances. NAT gateways are typically used to enable instances in a private subnet to access the Internet for software updates, patching, and other common Internet-based activities.
VPC Endpoint
A VPC endpoint is a private connection between your Amazon Virtual Private Cloud (Amazon VPC) and supported AWS services or VPC endpoint services powered by PrivateLink. VPC endpoints allow you to securely access AWS services and VPC endpoint services from within your VPC without requiring an Internet Gateway, a NAT device, or a VPN connection.

There are two types of VPC endpoints:
Interface endpoints: These are elastic network interfaces with private IP addresses that are connected to your VPC, and allow you to connect to supported AWS services and VPC endpoint services powered by PrivateLink.
Gateway endpoints: These are horizontally scalable, highly available VPC components that allow you to connect to Amazon S3 and DynamoDB.
VPC endpoints are useful in a number of situations, such as:
Allowing instances in your VPC to access AWS services and VPC endpoint services without requiring an Internet connection.
Providing a more secure and scalable way to access AWS services and VPC endpoint services from within your VPC.
Reducing the dependency on Internet connectivity and the associated costs of data transfer.
Overall, VPC endpoints are a useful tool for securely accessing AWS services and VPC endpoint services from within your VPC, and can be helpful in a variety of situations where you need to access these services from within your VPC.
Prefix List

A prefix list is a collection of IP address ranges (prefixes) that are associated with an Amazon Virtual Private Cloud (Amazon VPC) or an on-premises network. Prefix lists can be used to specify the allowed prefixes for a VPC peering connection, a VPC endpoint, or a VPC endpoint service powered by PrivateLink.
A prefix list consists of a set of prefixes, each of which specifies an IP address range. You can create prefix lists in Amazon VPC and specify the prefixes that you want to allow or deny for a VPC peering connection, a VPC endpoint, or a VPC endpoint service powered by PrivateLink.
Prefix lists are useful in a number of situations, such as:
Specifying the allowed prefixes for a VPC peering connection, to control the traffic between the peered VPCs.
Specifying the allowed prefixes for a VPC endpoint or a VPC endpoint service powered by PrivateLink, to control the traffic to and from the endpoint or the service.
Providing a more fine-grained way to specify the allowed prefixes for a VPC peering connection, a VPC endpoint, or a VPC endpoint service powered by PrivateLink, as compared to using security groups or network ACLs.
Overall, prefix lists are a useful tool for specifying the allowed prefixes for a VPC peering connection, a VPC endpoint, or a VPC endpoint service powered by PrivateLink, and can be helpful in a variety of situations where you need to control the traffic to and from these resources.
Private Link
AWS PrivateLink is a service that enables you to access services over a private network connection. It allows you to create a private connection between your Amazon Virtual Private Cloud (Amazon VPC) and supported AWS services, as well as services powered by AWS PrivateLink.
With AWS PrivateLink, you can create a private connection between your VPC and the supported AWS service or service powered by AWS PrivateLink. This connection is established over the Amazon network, and does not require an Internet Gateway, a NAT device, or a VPN connection.


AWS PrivateLink is useful in a number of situations, such as:
Allowing you to access supported AWS services and services powered by AWS PrivateLink over a private network connection.
Providing a more secure and scalable way to access supported AWS services and services powered by AWS PrivateLink from within your VPC.
Reducing the dependency on Internet connectivity and the associated costs of data transfer.
Overall, AWS PrivateLink is a useful tool for securely accessing supported AWS services and services powered by AWS PrivateLink over a private network connection, and can be helpful in a variety of situations where you need to access these services from within your VPC.
DHCP Options
DHCP (Dynamic Host Configuration Protocol) options are settings that are used to configure the behavior of DHCP clients, which are devices that use DHCP to obtain IP addresses and other network configuration settings automatically.
In Amazon Virtual Private Cloud (Amazon VPC), you can create a set of DHCP options and associate them with your VPC. The DHCP options specify the network configuration settings that will be provided to the DHCP clients in your VPC, such as the domain name, the DNS servers, and the NTP servers.
You can create DHCP options using the Amazon VPC console, the AWS CLI, or the Amazon VPC API. You can also modify the DHCP options for your VPC at any time.
Overall, DHCP options are an important tool for configuring the behavior of DHCP clients in your VPC, and can be useful in a variety of situations where you need to specify the network configuration settings for your VPC.
VPC Peering
VPC peering is a feature of Amazon Virtual Private Cloud (Amazon VPC) that enables you to connect two VPCs and allow the instances in those VPCs to communicate with each other as if they are within the same network.
With VPC peering, you can create a direct network connection between two VPCs, allowing the instances in those VPCs to communicate with each other using private IP addresses. This can be useful in a number of situations, such as:
Allowing instances in different VPCs to communicate with each other, without the need for an Internet connection or a VPN connection.
Enabling you to create a multi-tier application that spans multiple VPCs, without the need for a VPN connection or an Internet connection.
Providing a more secure and scalable way to connect two VPCs, compared to using an Internet connection or a VPN connection.
To create a VPC peering connection, you must request a peering connection and have the owner of the peer VPC accept the request. You can then create routes in the route tables of the VPCs to allow the instances in the VPCs to communicate with each other.
Transit Gateway
An AWS Transit Gateway is a network transit hub that you can use to interconnect your Amazon Virtual Private Clouds (VPCs) and on-premises networks. A Transit Gateway acts as a router that routes traffic between the connected VPCs and on-premises networks, and can scale to support thousands of VPCs and on-premises networks.

With a Transit Gateway, you can simplify your network architecture and reduce the complexity of managing multiple VPCs and on-premises networks. You can use a Transit Gateway to connect VPCs and on-premises networks using VPC peering or VPN connections, and create a central hub for routing traffic between the connected VPCs and on-premises networks.
A Transit Gateway is a horizontally scalable, highly available VPC component that you can use to connect VPCs and on-premises networks. You can use a Transit Gateway to connect VPCs and on-premises networks in a single AWS Region, or in multiple AWS Regions.
VPN
A virtual private network (VPN) is a private network that is built on top of a public network, such as the Internet. A VPN allows you to create a secure connection between two or more devices, and to transmit data over the public network as if it were a private network.
In Amazon Web Services (AWS), you can use a VPN to securely connect your on-premises network to an Amazon Virtual Private Cloud (Amazon VPC). This allows you to extend your on-premises network into the cloud, and to communicate with the instances in your Amazon VPC as if they were on the same network as your on-premises network.

To create a VPN connection in AWS, you must create a virtual private gateway and attach it to your VPC, and then create a customer gateway and configure it on your on-premises network. You can then create a VPN connection between the virtual private gateway and the customer gateway, and specify the routing information for the connection.
Direct Connect
AWS Direct Connect is a network service that enables you to establish a dedicated network connection from your on-premises data center to AWS. With AWS Direct Connect, you can establish a private, high-bandwidth connection between your on-premises data center and an AWS region, which can reduce your network costs, increase bandwidth throughput, and provide a more reliable connection to AWS.

To use AWS Direct Connect, you must create a virtual interface and specify the AWS region that you want to connect to. You can then establish a connection between your on-premises data center and the virtual interface using a direct connection or a cross-connect.
AWS Direct Connect is useful in a number of situations, such as:
Reducing your network costs by eliminating the need to use the public Internet to connect to AWS.
Increasing bandwidth throughput by providing a dedicated connection to AWS.
Providing a more reliable connection to AWS, as compared to using the public Internet.
Overall, AWS Direct Connect is a useful tool for establishing a dedicated network connection from your on-premises data center to AWS, and can be helpful in a variety of situations where you need to reduce your network costs, increase bandwidth throughput, or provide a more reliable connection to AWS.
VPC Flow Log
VPC Flow Logs is a feature of Amazon Virtual Private Cloud (Amazon VPC) that enables you to capture information about the IP traffic flowing in and out of your VPC network interfaces. With VPC Flow Logs, you can log the accepted and rejected traffic for your VPC, VPC subnets, and your Amazon Elastic Compute Cloud (Amazon EC2) instances.
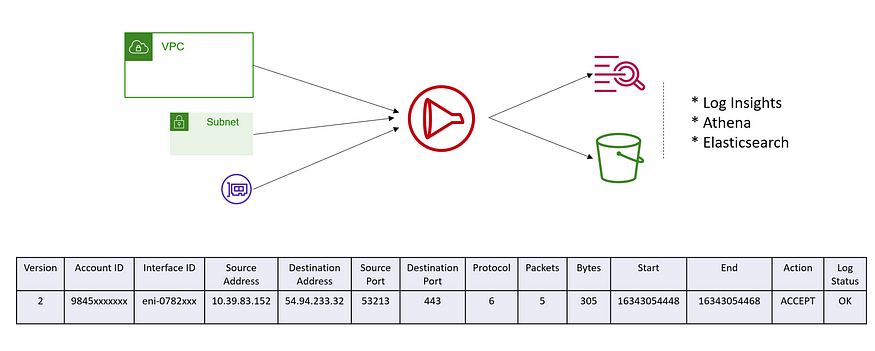
VPC Flow Logs can be useful in a number of situations, such as:
Debugging network issues.
Monitoring the traffic that is flowing in and out of your VPC.
Security and compliance purposes.
To create VPC Flow Logs, you must specify a destination for the log data (such as an Amazon CloudWatch Logs log group or an Amazon S3 bucket), and then specify the VPC, VPC subnets, or Amazon EC2 instances that you want to capture traffic for. You can then view the flow logs in the specified destination.
Overall, VPC Flow Logs is a useful tool for capturing information about the IP traffic flowing in and out of your VPC network interfaces, and can be helpful in a variety of situations where you need to debug network issues, monitor traffic, or meet security and compliance requirements.
Traffic Mirroring
AWS Traffic Mirroring is a feature of Amazon Virtual Private Cloud (Amazon VPC) that enables you to replicate network traffic from a source Amazon Elastic Network Interface (ENI) to a destination ENI. With Traffic Mirroring, you can replicate the traffic from a source ENI to a destination ENI in the same VPC, or in a different VPC.

Traffic Mirroring can be useful in a number of situations, such as:
Debugging network issues.
Monitoring network traffic for security or compliance purposes.
Analyzing network traffic for performance or optimization purposes.
To use Traffic Mirroring, you must create a Traffic Mirroring session and specify the source and destination ENIs for the session. You can then specify the traffic that you want to mirror, such as all traffic or traffic from specific IP ranges or port ranges.
Overall, Traffic Mirroring is a useful tool for replicating network traffic from a source ENI to a destination ENI, and can be helpful in a variety of situations where you need to debug network issues, monitor network traffic, or analyze network traffic.
Reachability Analyzer
AWS Reachability Analyzer is a feature of Amazon Virtual Private Cloud (Amazon VPC) that enables you to test the reachability of your VPC resources from your on-premises network or from other VPCs. With Reachability Analyzer, you can test the connectivity between your on-premises network or VPCs, and your Amazon Elastic Compute Cloud (Amazon EC2) instances, Amazon Relational Database Service (Amazon RDS) instances, and Amazon Elastic Container Service (Amazon ECS) tasks.

Reachability Analyzer is useful in a number of situations, such as:
Debugging network connectivity issues.
Verifying the connectivity between your on-premises network or VPCs and your Amazon EC2 instances, Amazon RDS instances, and Amazon ECS tasks.
Testing the reachability of your VPC resources from different locations.
To use Reachability Analyzer, you must create a reachability test and specify the source and destination VPCs or on-premises networks, as well as the Amazon EC2 instances, Amazon RDS instances, or Amazon ECS tasks that you want to test reachability for. Reachability Analyzer will then test the connectivity between the source and destination, and provide the results of the test.
Overall, Reachability Analyzer is a useful tool for testing the reachability of your VPC resources from your on-premises network or from other VPCs, and can be helpful in a variety of situations where you need to debug network connectivity issues or verify the connectivity between your VPCs and your Amazon EC2 instances, Amazon RDS instances, or Amazon ECS tasks.
Shared VPC design
A shared VPC is a Amazon Virtual Private Cloud (Amazon VPC) that is shared among multiple AWS accounts. With a shared VPC, you can allow multiple AWS accounts to use the resources in your VPC, such as Amazon Elastic Compute Cloud (Amazon EC2) instances, Amazon Relational Database Service (Amazon RDS) instances, and Amazon Elastic Container Service (Amazon ECS) tasks.

There are two types of accounts in a shared VPC:
The owner account: This is the account that owns the shared VPC, and is responsible for creating and managing the shared VPC.
The member accounts: These are the accounts that are allowed to use the resources in the shared VPC.
To design a shared VPC, you should consider the following:
The AWS accounts that will be member accounts in the shared VPC.
The VPC resources that the member accounts will be allowed to use.
The security measures that you will put in place to protect the shared VPC resources.
The networking configuration of the shared VPC, including the IP address ranges, subnets, and route tables.
Overall, a shared VPC is a useful tool for allowing multiple AWS accounts to use the resources in your VPC, and can be helpful in a variety of situations where you need to share VPC resources among multiple AWS accounts.